Cross-Site Scripting (XSS) in .NET
Cross Site Scripting(xss) occurs whenever application allows untrusted input and send it back to the client browser without validating the input. Through XSS attackers executes the script in the client browser which can hack user cookies, user sessions and redirect the user to the malicious web sites.
As per Website Security Statistics Report which is delivered by WhiteHat Security, 65% of websites affected with XSS vulnerabilities.
XSS generally happens whenever we allows the html input from the client. We can restrict the html input by using RegularExpression Validator as shown below. By restricting the html input we can avoid cross-site scripting(XSS).
<%@ Page Language="C#" AutoEventWireup="true" CodeFile="Default.aspx.cs" Inherits="_Default" ValidateRequest="false" %>
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head runat="server">
<title>Cross Site Scripting in .Net</title>
</head>
<body>
<form id="form1" runat="server">
<div>
Input: <asp:TextBox ID="txtInput" TextMode="MultiLine" runat="server"></asp:TextBox><br />
<asp:RegularExpressionValidator id="RegularExpressionValidator1" runat="server" ErrorMessage="RegularExpressionValidator"
validationexpression='([^<>\"\^])*' ControlToValidate="txtInput" />
<asp:Button ID="btn" runat="server" OnClick="btn_Click" Text="Click" /><br /><br />
Ouput: <asp:Literal ID="litOutput" runat="server"></asp:Literal><br />
</div>
</form>
</body>
</html>
By entering the input as <script type="text/javascript">alert('ok');</script>, Regular Expression Validator displays error message as shown below.

But sometimes you may have requirement to allow the html input from the users, but your application affects with the XSS. In this article, we are going to discuss about how Cross-Site Scripting(XSS) occurs in .Net and how to avoid Cross-Site Scripting(XSS) in Asp.net .Net. For example we create the simple Asp.Net application which has one textbox, button and one literal control as shown below.
<%@ Page Language="C#" AutoEventWireup="true" CodeFile="Default.aspx.cs" Inherits="_Default"%>
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head runat="server">
<title>Cross Site Scripting in .Net</title>
</head>
<body>
<form id="form1" runat="server">
<div>
Input: <asp:TextBox ID="txtInput" TextMode="MultiLine" runat="server"></asp:TextBox><br />
<asp:Button ID="btn" runat="server" OnClick="btn_Click" Text="Click" /><br /><br />
Ouput: <asp:Literal ID="litOutput" runat="server"></asp:Literal><br />
</div>
</form>
</body>
</html>
If you enter the input as <script type="text/javascript">alert('ok');</script> in text area you will get the error as "A potentially dangerous Request.Form value was detected from the client (txtInput="<script type="text/j...")" because asp.net control will not validate html input. To allow the html input we have to disable the request validation by changing the ValidateRequest attribute value as false as shown below at page level.
<%@ Page Language="C#" AutoEventWireup="true" CodeFile="Default.aspx.cs" Inherits="_Default" ValidateRequest="false" %>
We can disable request validation by changing the ValidateRequest value in web.config file as shown below.
<configuration>
<system.web>
<pages validateRequest="false"></pages>
</system.web>
......
</configuration>
But disabling the request validation is not recommended, disable the ValidateRequest per page level only where ever required.
Now enter the input as <script type="text/javascript">alert('ok');</script> after disabling the ValidateRequest and click on button and output displays the alert box. Displaying the alert box is not major issue, but through Cross-Site Scripting even hacker can get cookies data and can redirect to malicious web sites.
By entering the <script type="text/javascript">alert(document.cookie);</script> input we can get the cookie data as shown below.
using System;
using System.Web;
public partial class _Default : System.Web.UI.Page
{
protected void Page_Load(object sender, EventArgs e)
{
if (!IsPostBack)
{
HttpCookie tempCookie = new HttpCookie("sessionkey", "hello");
Response.Cookies.Add(tempCookie);
}
}
protected void btn_Click(object sender, EventArgs e)
{
litOutput.Text = txtInput.Text;
}
}
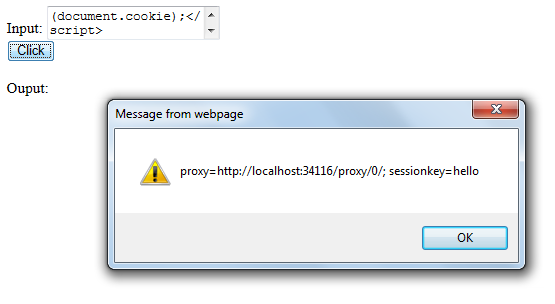
By entering the input as <script type="text/javascript">window.location.href="";</script>, user redirected to mentioned applications. Here we provided our blog, but hacker can redirect to malicious web sites.
To avoid the excuting of script input we have to encode the input before displaying it to browser as shown below.
protected void btn_Click(object sender, EventArgs e)
{
litOutput.Text = HttpUtility.HtmlEncode(txtInput.Text);
}
Now enter script input as <script type="text/javascript">alert(document.cookie);</script> and the output is display as shown below, it just display as text.

